I was recently sent this video by a friend who wanted to know if this was “legit”:
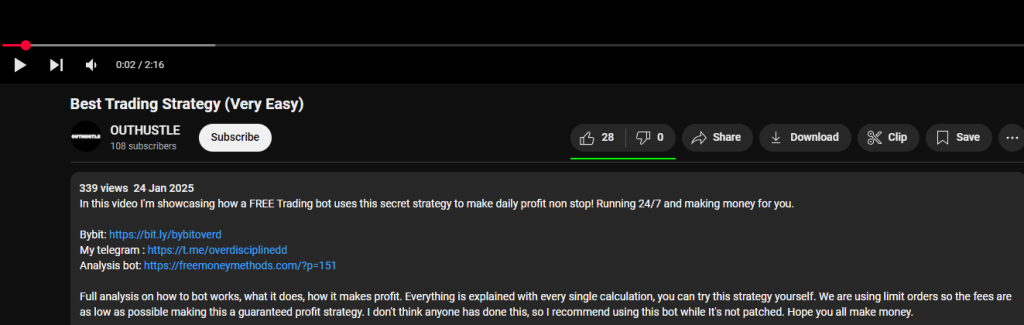
The video advertises a trading bot that automates trades between crypto USDT and USDC, taking advantage of small price differences to generate guaranteed profit. Sounds too good to be true right? Let’s examine this so-called trading bot using publicly available malware analysis tools, along with insights from the “Practical Malware Analysis & Triage” course I recently completed through TCM Security. I won’t be diving too deep into the analysis, but I will conclude if it is malicious or not.
The video description has a link to another link that lead me to a Google Drive file download.
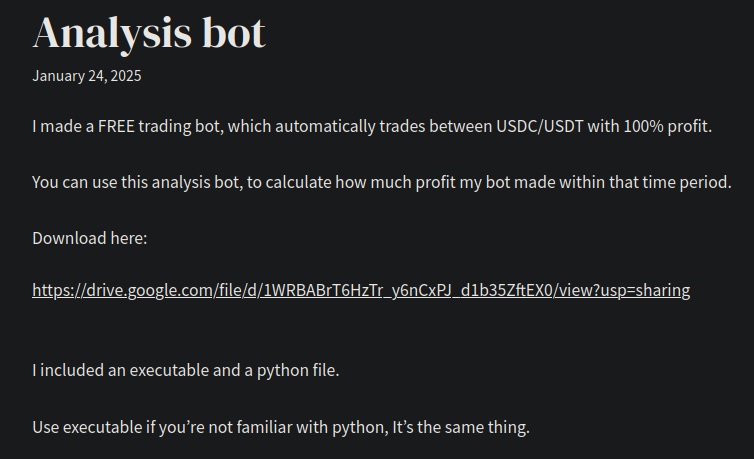
On download, we get a little message saying it’s too large for Google to scan for viruses. This is just the default message since Google cannot scan zipped files for viruses.
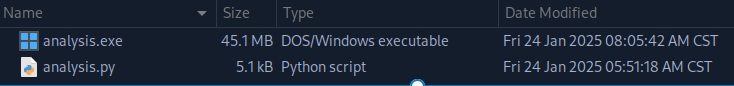
Once the zip file is extracted, we get 2 files, one executable and one python file. I checked analysis.py and it doesn’t look to do anything at all really, so maybe it’s an illusion of free will – the python script wouldn’t work for you, so you would need to run analysis.exe to run the trading bot instead to get the guaranteed “free monies“.
Static Analysis
First, let’s first take a static look at the binary using PeStudio:
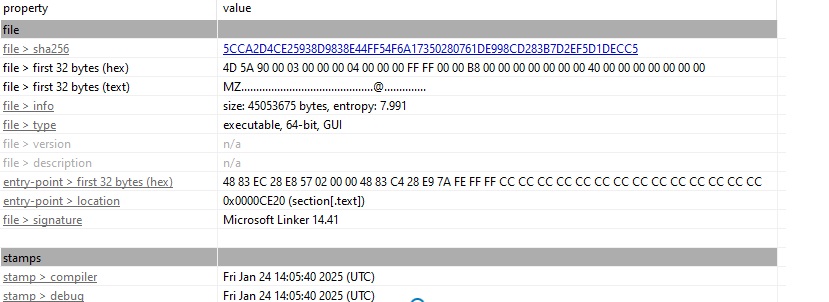
Top level informational stuff such as hashes, magic bytes and architecture, and we can see that it was very recently created only a couple of weeks ago.
Checking the binary strings, I can’t draw on anything that pops out right away. Just some Window API calls.
Lets next check what the libraries and WindowsAPIs the executable imports. We will again use PeStudio for this.
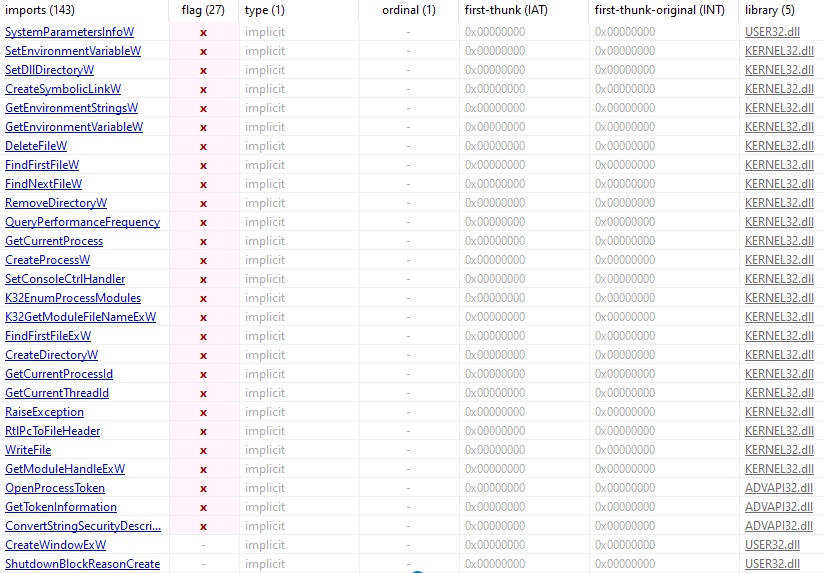
We can see numerous WindowsAPI imports that have been flagged by the application as being potentially malicious. Although, just because they have been flagged by PEStudio, it doesn’t mean that the usage is malicious. Plenty of legitimate executables might call upon the same libraries and API calls.
Though for a simple “trading bot”, it sure does call upon a LOT of WindowsAPIs. If we take a look at https://malapi.io/ (a handy online resource to map Windows APIs to common techniques used by malware), we can see a few APIs that are linked to malware type activity, but we cannot be sure of anything yet.
Next we run capa. Capa, a program created by Mandiant, detects malicious capabilities in suspicious programs by using a set of rules. It translates the technical information in a binary into simple, human-readable information, mapping to the ATT&CK framework.
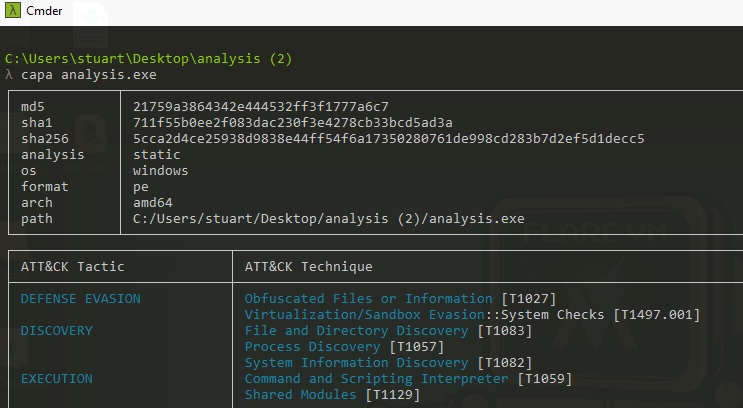
We see some interesting high level information about the executable already. At first glance it has numerous detections of suspicious actions it can perform. For example, sandbox evasion techniques, meaning that if it detects that it is running on a virtual machine or if it thinks it is being analyzed, it won’t behave in the same way as it would on a normal system to bypass detection. This is not your everyday executable.
The next output provided is the Malware Behavioral Catalog (MBC) Objectives and Behaviors.
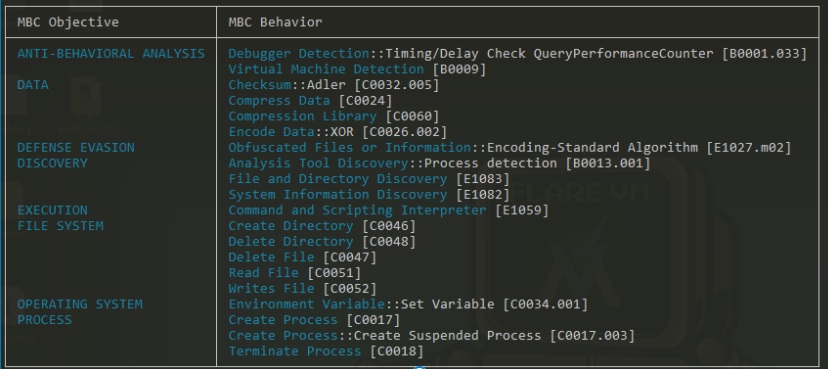
Again there is a lot going on here.
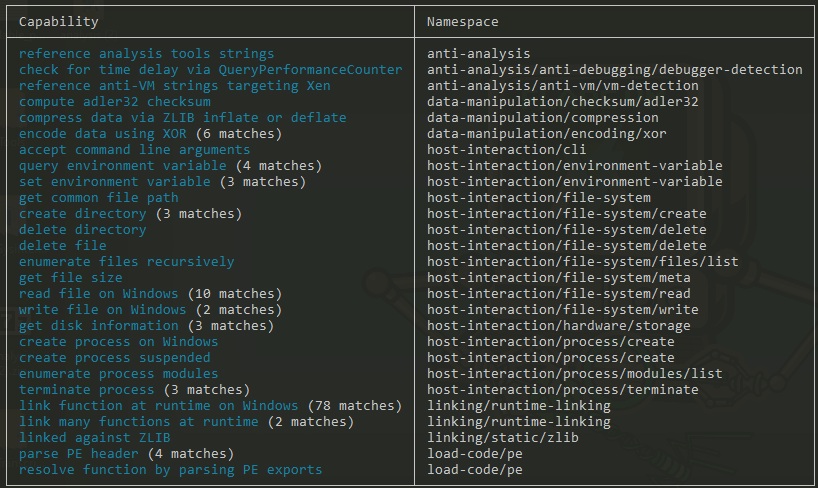
Based on what is seen so far on just the static binary examination, we can conclude that this certainly isn’t a simple cryptocurrency trading bot, but rather something malicious with something else is going on behind the scenes. Let’s dive into the dynamic analysis.
Dynamic Analysis
I uploaded the file to VirusTotal and Hybrid Analysis, the first time either platforms have seen this sample.
VirusTotal: https://www.virustotal.com/gui/file/5cca2d4ce25938d9838e44ff54f6a17350280761de998cd283b7d2ef5d1decc5
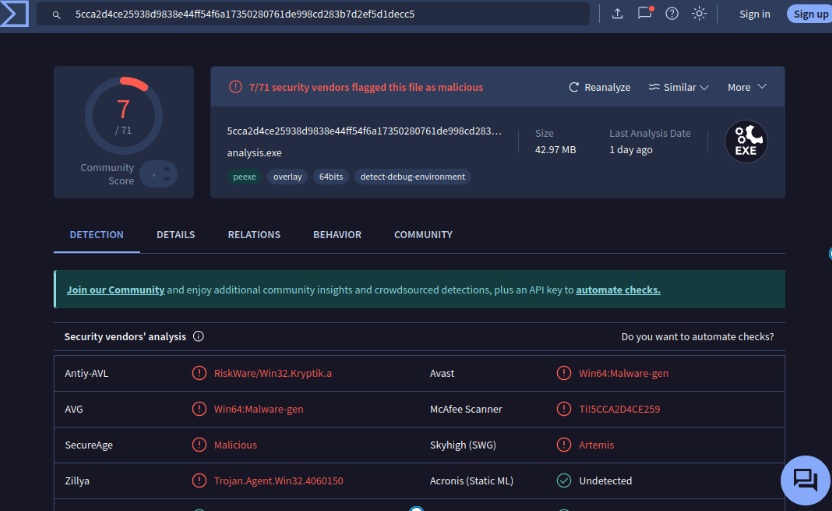
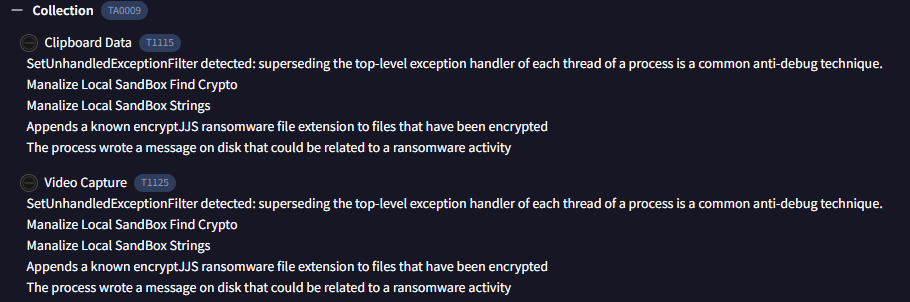
The detections show multiple instances of highly suspicious activity, such as accessing your clipboard and monitoring your screen. This behavior goes well beyond what would be expected from a typical trading bot.
Hybrid Analysis Report: https://www.hybrid-analysis.com/sample/5cca2d4ce25938d9838e44ff54f6a17350280761de998cd283b7d2ef5d1decc5/67a6a718efd3c8b9e40b128e
From the Hybrid Analysis report, there is almost too many indicators to count. Legitimate crypto trading bots typically don’t require such deep system access. Most notable Indicators include: Debugger Evasion, Screen Capture, File and Directory Discovery & Process Injection. I’m fairly confident that given enough time, the program would reach out to a C2 address to share the discovered data. One issue I’ve seen previously is that there is sometimes a time delay in sending data to the C2 address to avoid detection in 60 second malware analyzers. I would like very much to try any.run and extend the timer to fully see what It can do over a longer period of time- but I need a business email/ have to pay to use the service.
At this point, I’ve seen enough and told my friend to be more careful, especially when promised easy money making methods.
Conclusion
The malware poses a significant threat to cryptocurrency traders by exploiting common trader behaviors like storing or copying private keys. Its ability to gather sensitive information, such as clipboard contents and screenshots, highlight the importance of being cautious with unfamiliar software. To protect against such threats, it’s crucial for users to only download trusted applications, regularly update security measures and remain vigilant, especially on devices that is used to handle private keys. Ultimately, this analysis serves as a reminder to always question offers that seem too good to be true.
I have since reported the video to YouTube.
