My cloud-hosted VPS serves as a personal VPN server that also routes traffic through a Pi-hole to block ads and trackers—because, honestly, that’s the only way the internet is useable these days. It’s been running for a couple of years with little to no maintenance, and recently, I decided it was time to put my Security Analyst skills to good use and properly monitor and secure it. That said, I haven’t updated it in who knows how long, so I fully expect to find some unpatched vulnerabilities.
I want to ensure it’s hardened to the highest standard and that robust monitoring is in place to alert me to any suspicious activity. There are many ways to assess and strengthen my server’s security posture, but one approach that stands out to me is deploying an XDR solution called Wazuh.
Wazuh XDR (Extended Detection and Response) is an open-source security platform and SIEM (Security Information and Event Management) designed to help organizations detect and respond to threats across their infrastructure. It provides real-time monitoring of endpoints, cloud environments, and network activity, offering threat intelligence, automated responses, and alerting. While open-source, it delivers capabilities similar to premium XDR solutions like Microsoft Defender XDR and CrowdStrike Falcon.
The biggest advantage for me is that Wazuh is open-source, meaning I pay nothing to use it—aside from the server rental cost to host it. Of course, you can choose to deploy it on-premises if you prefer, but I opt for cloud hosting.
To start, I need to set up the master monitoring server that will collect logs from all connected devices. I deployed a new VPS with 2GB of RAM and 2 virtual CPUs—the minimum required for Wazuh. Since I’m not an organization monitoring hundreds of systems, I can keep my deployment relatively small.
Once I have an Ubuntu 22.04 VPS set up, I can prepare the system and install Wazuh using Docker. I’m following the official guide from Wazuh’s documentation: https://documentation.wazuh.com/current/deployment-options/docker/wazuh-container.html
sudo apt update
sudo apt install docker.io docker-compose -y
git clone https://github.com/wazuh/wazuh-docker.git -b v4.11.0
cd wazuh-docker/
cd single-node
docker-compose -f generate-indexer-certs.yml run --rm generator
docker-compose up -d
And that’s all the commands needed to spin up the Wazuh server. Just give it some time to process and complete the setup.
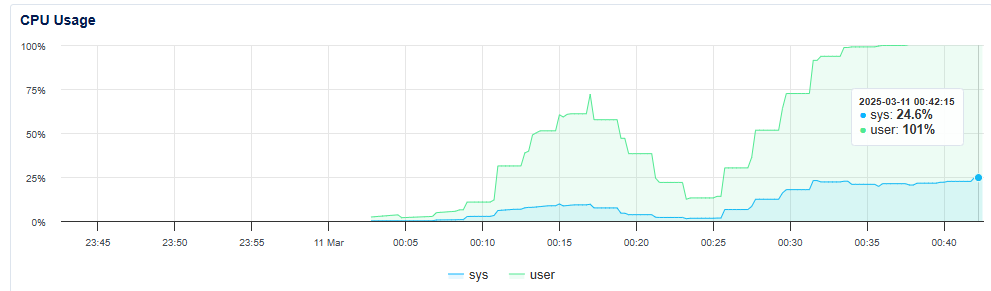

Anyway… when it’s calmed down, proceed to the Wazuh Dashboard at https://<VPS-IP-Address>
The default username and password for the Wazuh dashboard are admin and SecretPassword. (Change that password!)

This is the Dashboard you will see once you log in.
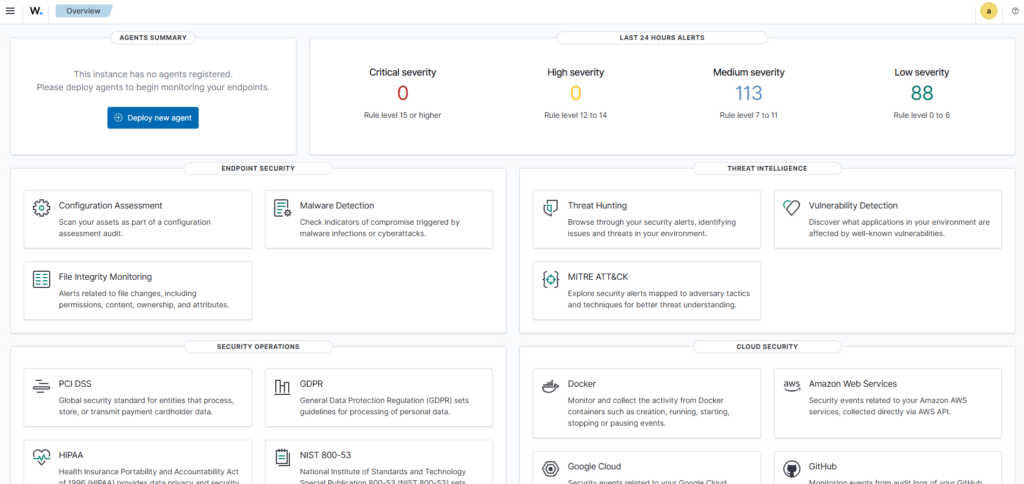
Next, I want to deploy Wazuh to my VPN Server to make it an “agent” to monitor.
Wazuh makes it easy to deploy to systems of any architecture and OS, just select what is applicable for your new agent:
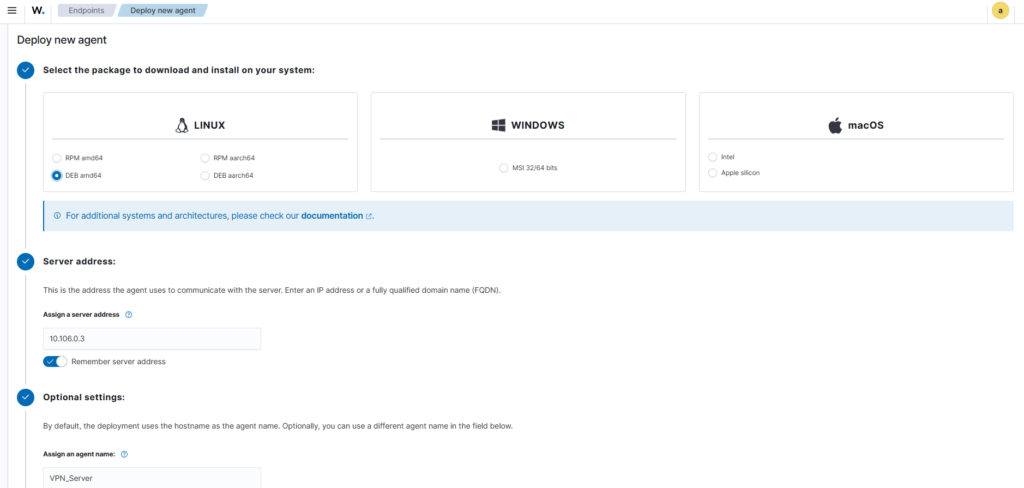
It will generate custom commands that you can easily copy and paste into the server you want to configure as an agent, while ensuring persistence through restarts.
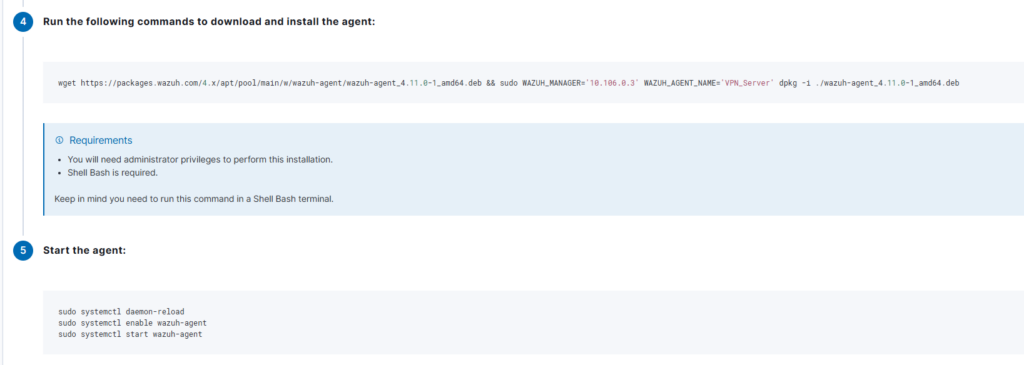
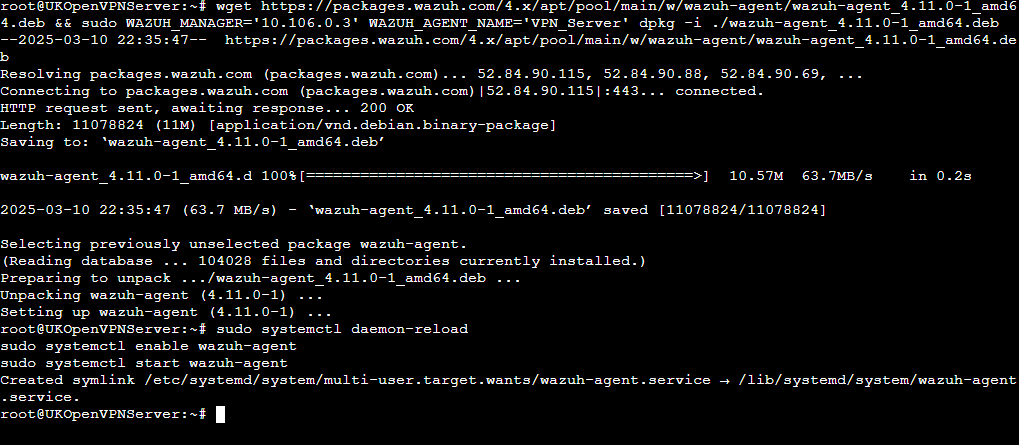
After pasting the provided commands into my VPN server, the agent quickly appears in the dashboard:
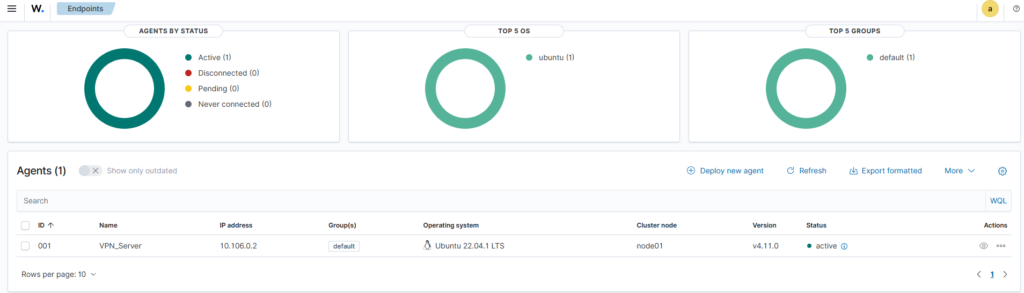
It’s as easy as that- just give it some time to scan the machine, and the dashboard will update—mine changed after a little while:
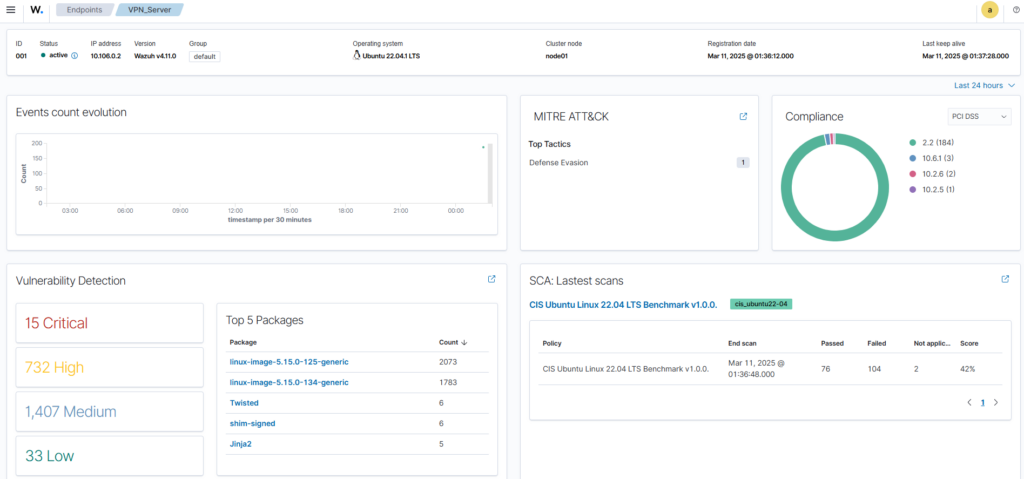
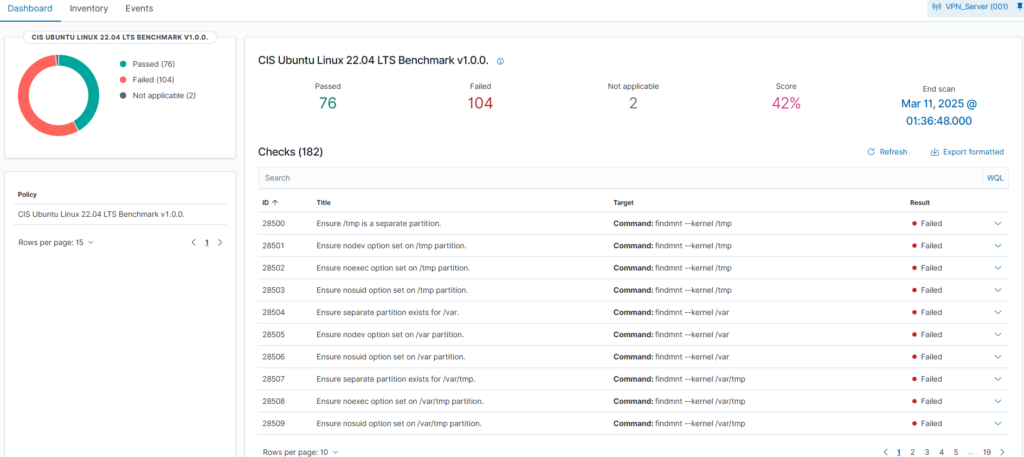
Right away, I can see on the agent dashboard critical vulnerabilities, issues related to the MITRE ATT&CK framework, and a CIS Benchmark.
Lets start with the CIS Benchmark, it’s noted that I’ve only a passing score of 42%, but what does this mean?
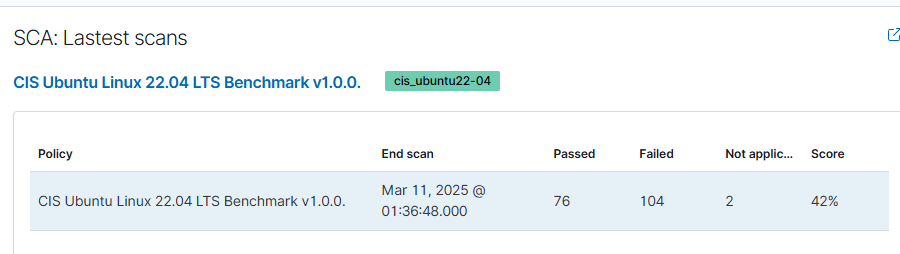
The CIS (Center for Internet Security) benchmarks provide configuration baselines and best practices for securely setting up a system. For more information, check out this CIS Benchmark guide: https://learn.microsoft.com/en-us/compliance/regulatory/offering-cis-benchmark
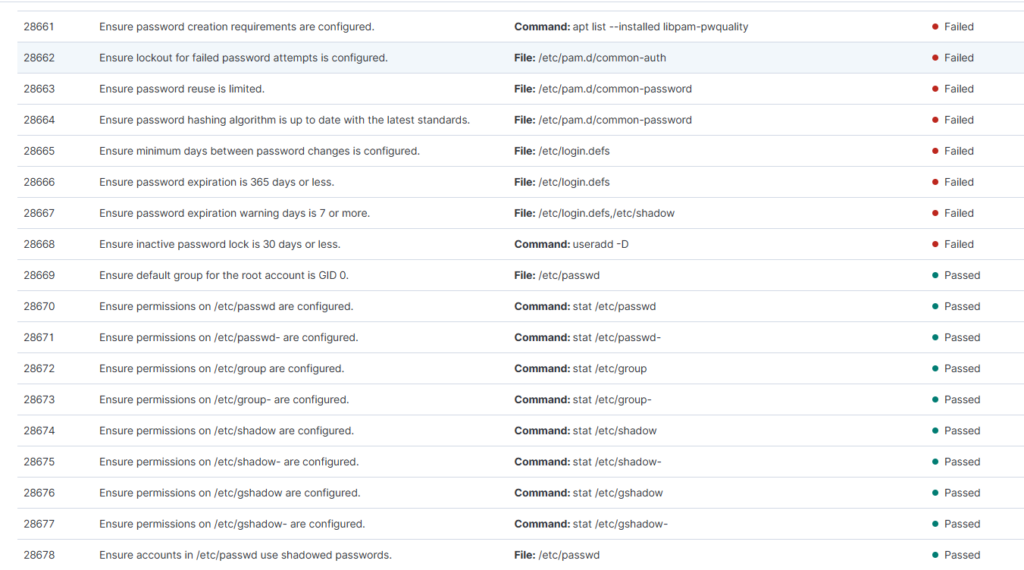
The benchmark results for my VPN Server highlight both the best practices my agent passed and the ones it failed, along with the exact commands needed to fix the identified issues.
For example, it highlights that the /tmp directory could be exploited by attackers for file storage and execution. It recommends the exact commands and steps needed to fix this specific issue to tighten up my overall security posture:
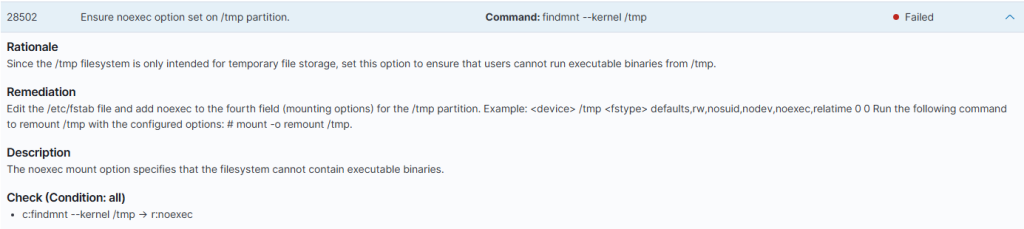
Great at helping to harden my system! Now to look at Vulnerability Detections, I seem to have 15 critical detections that need to be looked at:
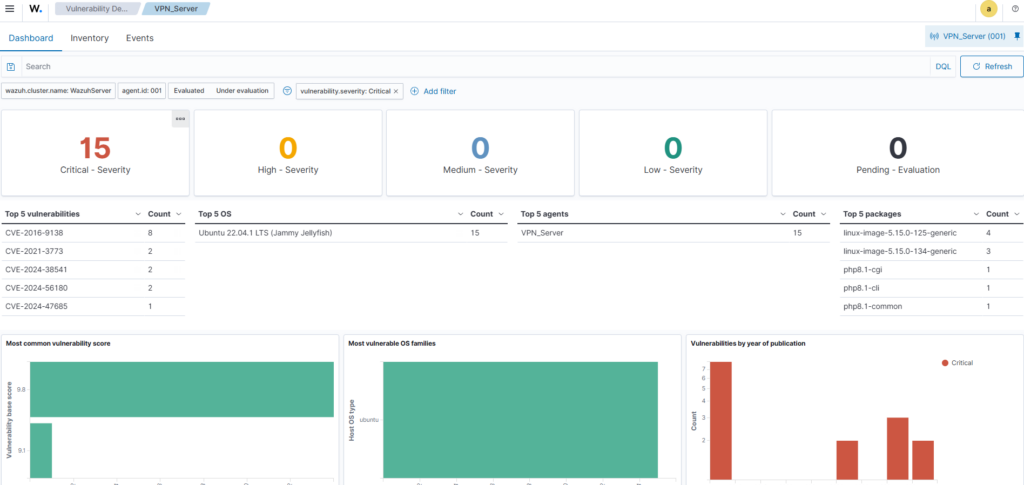
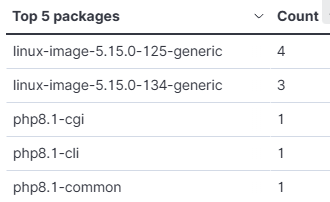
It has highlighted CVEs that my system may be susceptible to, along with the associated packages. It seems that mainly my Linux kernel and PHP package need updating.
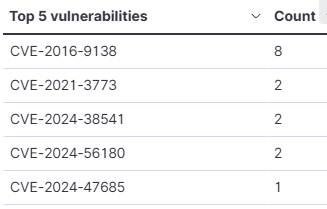
The most critical CVE from that list I could identify is CVE-2024-47685:
a critical security vulnerability identified in the Linux kernel’s netfilter module, particularly affecting the IPv6 components. This flaw allows an attacker to send malformed TCP packets, potentially leading to a kernel crash or information leak.
To rectify this, i issued a sudo update & upgrade command to update the kernel and packages. I’ll admit, I may have become a bit too complacent with my updates!
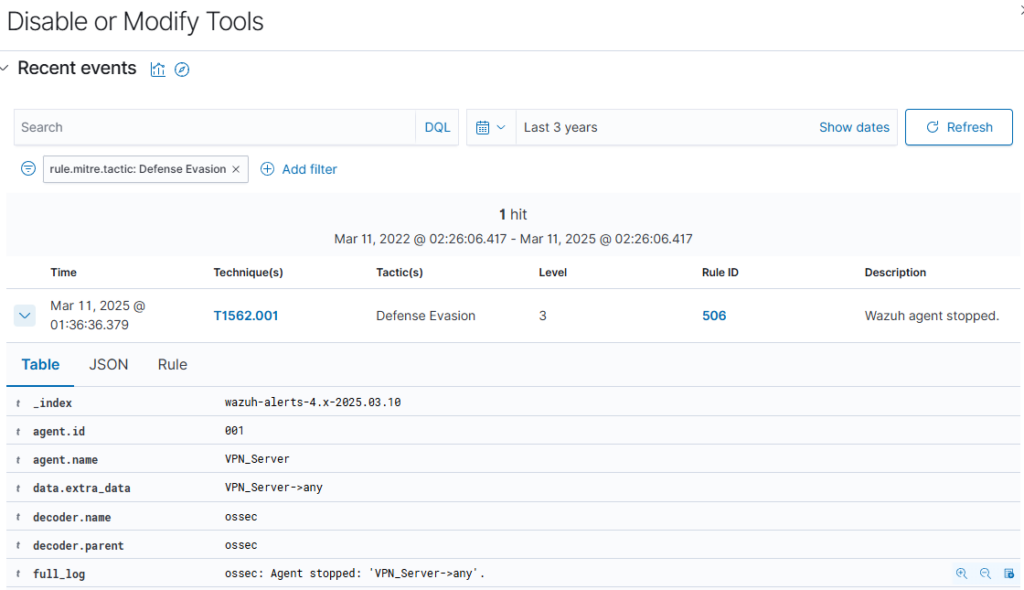
Next, I looked into MITRE ATT&CK detections, which got a hit on “Defense Evasion”.
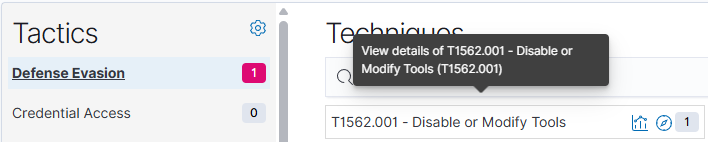
Looking deeper, I saw this was simply the detection of the newly deployed Wazuh agent stopping, an action which I performed myself earlier, but real attackers may disable monitoring apps to hide their tracks:
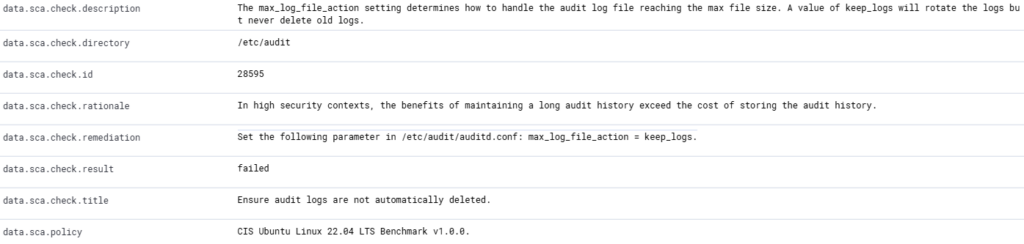
In terms of raw logs on my VPN server, I don’t have much history, as my log retention policy isn’t very comprehensive. During the CIS benchmark, it recommended adjusting the audit history length:
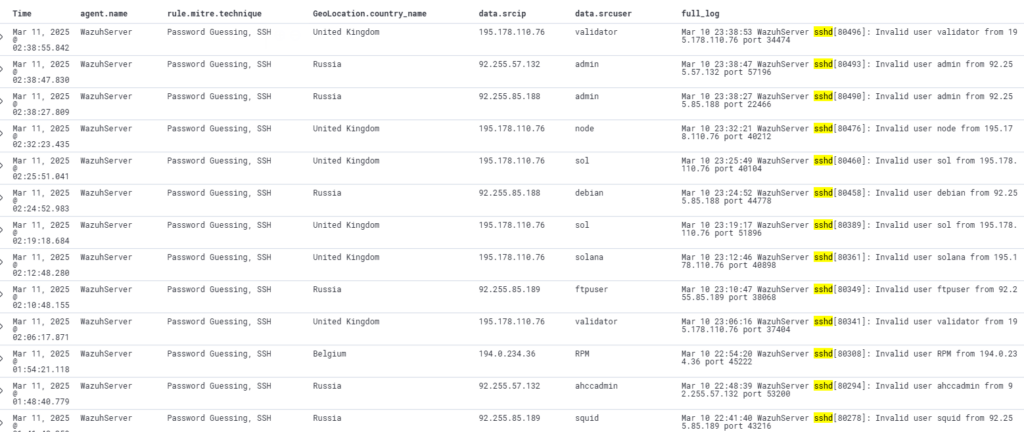
Interestingly, while experimenting with Wazuh, I noticed real-time brute force attacks targeting SSH from both Russia and the UK on my Wazuh Server VPS. It really shows that if you have a public-facing server on the internet, you’re bound to encounter uninvited interactions. This reminded me to deploy the same firewall configuration I use on my VPN server to the Wazuh server, blocking SSH access from all IPs except my own.
Next time, I want to try adding a Windows Server host with malware execution to see what kind of alerts pop up!
And finally, if I wanted to create monitoring rules, (maybe in the future, it will take time to write and test the queries) I have the ability to do so with multiple options to where I send the alert to for my immediate attention:
There are multiple “channels” I can send the alert notification to. There are popular messaging platforms such as Slack or Teams, and there is a custom webhook where you can POST your alert data, giving it the ability to integrate it with almost anything. It would be interesting to create a webapp that forwards the webhook POST alert data onto other messaging apps like WhatsApp.
Conclusion
Wazuh is a powerful, cost-effective open-source XDR solution, ideal for security monitoring, real-time alerting, and vulnerability detection. However, it’s not as robust as premium XDR solutions such as CrowdStrike Falcon. While Wazuh excels in log analysis and SIEM integration, Falcon goes beyond traditional signature-based detection, relying on behavioral-based detection methods, advanced analytics, and machine learning to identify and mitigate emerging threats in real-time. This makes Falcon better suited for active threat prevention with enterprise-level support, though at a higher cost. That said, Wazuh is the right choice for me and my environment, allowing me to implement robust monitoring and ensure my server is hardened to the highest standard without any additional cost.
